
Picture this: you are a first-year nurse with an unusual case that you and your colleagues have never seen at your hospital. To expedite the formulation of a treatment plan, you turn to a private Facebook group for nurses to which you belong. Since joining the 8,000-person closed group, you’ve witnessed your peers share information – with important details withheld – as to not break privacy laws, but as a means to generate group think on analysis and recommendations. You’ve seen first-hand how this group has helped a lot of nurses, so you decide to share the details of your case.
You proceed to post some important case details along with a portion of an MRI scan, of which you have removed all noticeable personally identifiable information (PII). You’ve seen many others carefully post images before, so you don’t hesitate to follow suit. Within minutes, the group starts weighing in, and your initial reaction is that you made the right decision. You may have helped your patient and looked good to your bosses at the same time.
What you aren’t aware of is that the group’s moderators have unintentionally granted access to someone claiming to be a nurse, but whose real purpose is to conduct reconnaissance to obtain information that can be used in an email spoofing attack. While it is true that the nurse may have helped expedite a treatment plan, it is also true that she involuntarily gave away about 80% of the information the attacker needs to develop a sophisticated spoofing attack. Now, with just a little more due diligence, the attacker can get everything he needs to construct and distribute an email that seems so realistic that even nurses who are suspicious of phishing attacks won’t be able to identify.
This isn’t a hypothetical scenario. Every day attackers are exploiting social media groups to capture private and personal information that can be used to launch email spoofing attacks.
Emails that masquerade as a trusted source
While bad actors use a variety of techniques to capture PII, email spoofing – an advanced phishing technique – is now commonly used against hospitals, according to HHS. Unfortunately, these attacks will only continue to increase and get easier, as we illustrated with the nurse unwittingly divulging PII to an attacker on social media. IndustryWeek reported that spoofing, along with and business email compromise, grew by 250 percent in 2018. Because these phishing attack techniques are so sophisticated, the consequences are also increasing. Today, the average cost of a cyber data breach for hospitals is almost $400 per medical record.
Email spoofing is very effective because it’s not readily detectable by traditional email security tools such as secure email gateways (SEGs) and is difficult for even phishing-trained humans to identify. Today there are two main types of spoofing attacks targeting hospitals. In Domain Name System (DNS) spoofing, altered DNS records are used to redirect online traffic to a fraudulent website that mimics the intended destination. From there, users are encouraged to log in to what they think is a legitimate account which then captures their credentials and other data for criminals to access the real network.
The second type of spoofing, IP Spoofing, is when an attacker uses tools to modify the source address in the IP packet header. This makes the receiving computer system think that the packet is from a trusted source, such as another computer on a legitimate network. Humana was hit with this type of attack in the summer of 2018 when hackers targeted participants in its Go365 wellness program. It only discovered the attack when it detected large numbers of failed login attempts from foreign IP addresses, according to an article in HIPPA Journal.
Protecting data from spoofing attacks
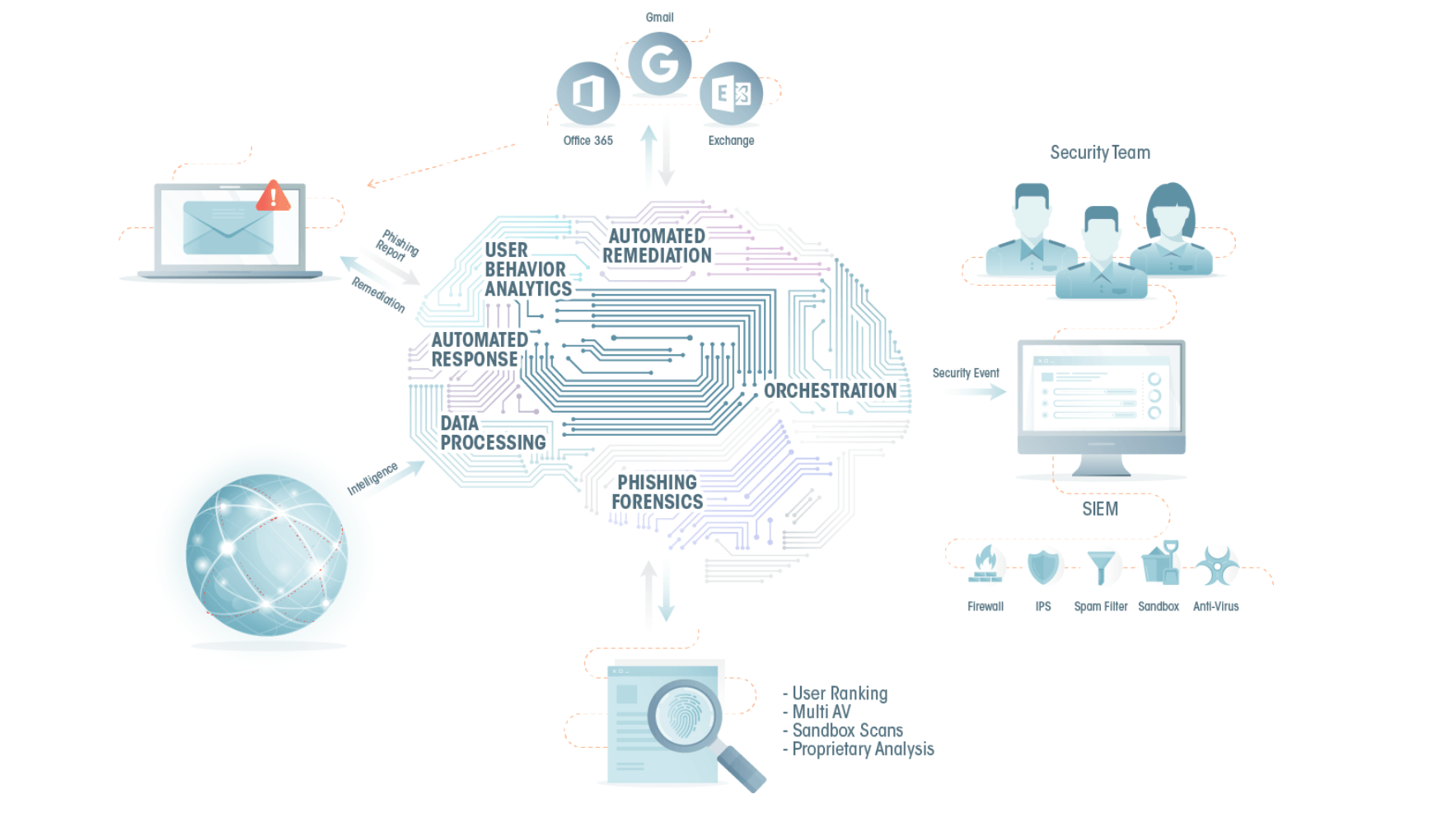
As these attacks persist, hospitals must act now to protect patient data and reduce risks. Here are 3 ways hospitals can mitigate the risk of email spoofing attacks.
1. Train employees to look for anomalies in communications
As attackers create new attack strategies to bypass systems, employees are often the best line of defense. Yet many hospitals aren’t keeping pace. A survey by KPMG found nearly 30 percent of healthcare and life sciences leaders said a lack of training was the biggest cybersecurity defensive weakness their organization faced. Better training won’t eliminate spoofing, but it can also help close the gap where there are signs. For example, accounts payable clerks may learn to spot trends around when and from where invoices come and view any deviance from the norm as suspicious. Employees across the organization should also confirm by phone when an email request, even from trusted superiors, seems out of the ordinary.
2. Create social media standards and hold employees accountable
With potentially hundreds of employees spread across a number of different departments, it’s vital for hospitals to implement a unified social media policy that all employees must adhere to. Limiting the use of vulnerable messaging apps and prohibiting the sharing of casework are easy places to start. Creating such a policy can help close the gap that hospitals have in understanding their internal and external risk factors.
3. Utilize anti-phishing technology in the mailbox
Spoofing attacks can now bypass some of the most advanced email security systems, so hospitals should add an additional layer of security in the mailbox itself. Mailbox level security uses predictive machine learning technology to detect attacks faster and alert users through inline messages. The best mailbox level security solutions use sender reputation scoring to monitor an individual’s communication habits and create a picture of what “normal” email communications should look like. The solution can then monitor mailboxes to flag irregular and suspicious communications.
At a time when email spoofing attacks targeting hospitals show no sign of slowing down, organizations must take a strong proactive approach towards security. Training your workforce, creating a social media policy and utilizing an anti-phishing solution can go a long way towards reducing the risks of spoofing and to educating employees about how even well-intentioned actions can be exploited for nefarious purposes.
Eyal Benishti is the CEO and Founder of IRONSCALES, an automated phishing prevention, detection, and response platform. Benishti has spent more than a decade in the information security industry, with a focus on software R&D for startups and enterprises. Before establishing IRONSCALES, he served as a security researcher and malware analyst at Radware, where he filed two patents in the information security domain.
