Editor’s Note: This post is sponsored by Samsung.
Unbeknownst to all, the healthcare industry is in possession of vast amounts of valuable data, while also being the most at-risk and easy to breach. Using outdated, interconnected electronic systems without a strong security plan contributes to this problem. According to Symantec’s 2016 Internet Security Threat Report, healthcare was the most targeted sector in 2015. To help ease the pain of this huge wound, Samsung and Booz Allen Hamilton partnered this year to create a mobile security assessment that can identify any gaps in company security protocols and help to improve overall security position. Illustrated in an informative infographic for easy reading, it covers the current state of a company’s security measurements, and the challenges and key areas to focus on for a more protected, mobile work platform.
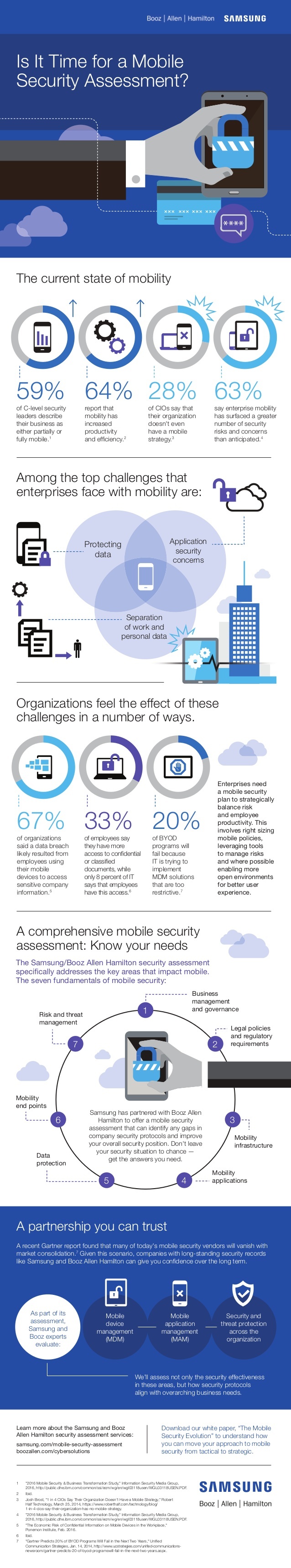
Currently, the state of mobility according to C-level security leaders breaks down as follows:
· 59% of C-level security leaders describe their business as either partially or fully mobile.
· 64% report that mobility has increased productivity and efficiency.
· 28% of CIOs state that their organization doesn’t have a mobile security strategy.
· 63% say enterprise mobility has surfaced a greater number of security risks and concerns than anticipated.
Among some of the top challenges that companies face with mobility security are protecting data, application concerns and separation of work and personal data.
Organizations feel the effect of these major challenges in a few ways:
· 67% of organizations said a data breach likely resulted from employees using their mobile devices to access sensitive company information.
· 33% of employees say they have more access to confidential or classified documents while only 8% of employees have this access according to company IT departments. (Organizations should always review and communicate with employees on how to properly manage confidential data on their mobile devices.)
· 20% of BYOD (Bring Your Own Device) programs will fail because IT departments are trying to implement MDM solutions that are too restrictive.
Enterprises need a mobile security plan to strategically balance risk and employee productivity. This involves right-sizing mobile policies, leveraging tools to manage risks, and where possible, enabling more open environments for better user experience. When looking at all the components involved, organizations need to manage and enable the reality, not the perception.
A comprehensive security assessment should inform organizations of their needs before employees gain mobility use. Companies should look at security analysis and planning, mechanism selection and testing and key architecture elements. Below are seven key fundamental pieces of a security assessment according to Samsung and Booz Allen Hamiliton:
1. Business management and governance – creating a MDM solution and team to oversee mobile uses
2. Legal policies and regulatory requirements – ensuring users are abiding by BYOD and PHI policies
3. Mobility infrastructure – getting practices involved on investing more money to make security a priority
4. Mobility applications – protecting PHI by denying downloads or by blocking unauthorized access to apps
5. Data protection – utilizing passwords, enabling encryption, wiping or remotely disabling mobile devices
6. Mobility endpoints – preventing data leakage with device encryption and other access control technologies
7. Risk and threat management – staying up-to-date and current on security and operating systems
Combating mobile security requires a developed mobile strategy that links business objectives to data safety. Be sure to implement plans that include mobile and wireless security, policies and standard reviews, in addition to legal and regulatory compliance checks. Having a solid mobile security plan that has all of these points is critical in our vulnerable industry of PHI.
For more content like this, follow Samsung on Insights, Twitter, LinkedIn, YouTube and SlideShare.
Source: https://insights.samsung.com/2016/10/14/is-it-time-for-a-mobile-security-assessment/
