
Editor’s Note: This post is co-written by David Wong, Managing Director of Bulger Partners, an advisory firm that specializes in healthcare IT and Mike Kavis, VP/Principal Architect for Cloud Technology Partners.
In 2009, the HITECH Act mandated that not only covered entities but also business associates would be subject to periodic audits as a means to ensure that both are complying with HIPAA Rules. The first phase of these audits, taking place between 2011 and 2012 and involving 115 covered entities, revealed abysmal results. Only 13 entities passed without any negative findings, and over 980 compliance issues were discovered. One-third of these violations were simply due to ignorance of HIPAA requirements.
As the HHS prepares for its second set of audits, this time including 50 business associates, a thorough understanding of HIPAA compliance is more important than ever for companies that handle protected health information. Alongside understanding the requirements of HIPAA compliance, organizations should choose a compliance solution that is most appropriate for their data volume and usage, as well as existing capabilities.
In this article, we explore the pros and cons of each approach, how companies should prepare for forthcoming HIPAA audits, and a few examples of successful and not-so-successful HIPAA compliance initiatives.
HITECH Has Changed the Regulatory Environment for Business Associates
Healthcare-focused technology companies that access electronic protected health information (ePHI, often referred to simply as PHI) have been hit especially hard by the HITECH Act. Such companies, defined as business associates (BAs), are now directly liable under HIPAA rules and could be subject to civil and criminal penalties for failing to meet new standards. This is a significant departure from pre-HITECH HIPAA, when all responsibility and liability fell on covered entities (health care providers, health plans, and clearinghouses). The change should come as no surprise: almost two-thirds of historical data breaches involved a BA.
The penalty for violations of a single provision can reach up to $1.5 million, and fines can add up if an organization has multiple infractions. Granted, these fines are immaterial compared to potential reputational damage. In July 2015, UCLA Health System acknowledged that hackers may have accessed sensitive information on up to 4.5 million patients. Just months before that, Anthem — the second largest health insurer in the US — revealed a breach of up to 80 million customer records. It is difficult to imagine patients trusting either of these organizations in the near future. IDC predicts one in three individuals will have their healthcare records compromised by cyber attacks in 2016, and no organization wants to be associated with those breaches.
Figure 1. HIPAA Breach Costs You Should Be Aware Of
The graph below illustrates cost components beyond the fines imposed by HIPAA/HITECH. Lost business has potentially the most severe financial consequences and has steadily increased over the past three years. This cost component includes the abnormal turnover of customers, increased customer acquisition activities, reputation losses and diminished goodwill.
Source: 2015 Cost of Data Breach Study
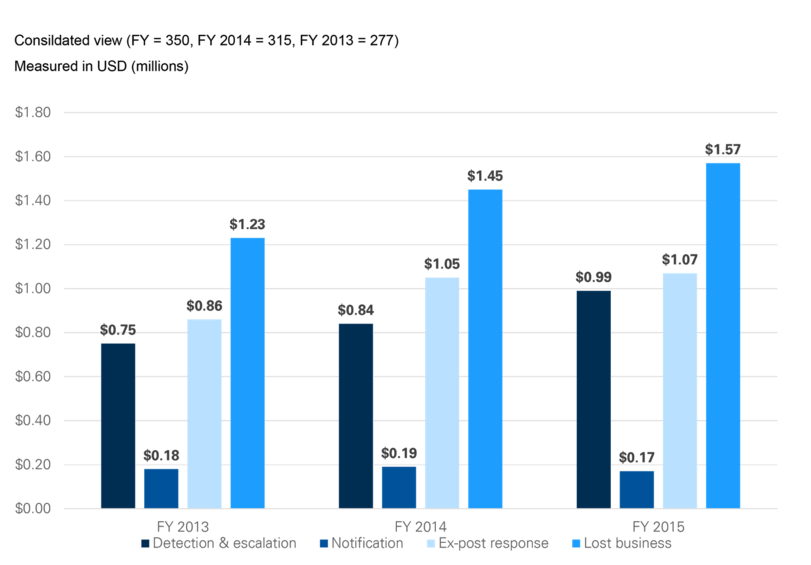
Nonetheless, given the limited flexibility of the healthcare system, it is unlikely that patients will switch insurers or providers in response to a data breach. The same does not hold for covered entities (CEs) and the BAs they engage. We have noticed that CEs now have more rigorous expectations of BAs. Often, they will look for a large and reputable existing client base, comprehensive evidence of HIPAA compliance, and demonstrated understanding of the intricacies of HIPAA and HITECH. Fail to meet these standards and a healthcare technology company may find itself boxed out of the market. Understandably, the current market and regulatory landscape has many operators asking, how exactly do I go about achieving HIPAA compliance?
Preparing for HIPAA Compliance
There is no single path to HIPAA compliance. Several factors will influence an organization’s choice for compliance, including: organizational size and complexity, volume of PHI, role of PHI in business workflows, and the organization’s team and platform capabilities. Given the HIPAA focus on security and privacy compliance, there is a natural tendency to prioritize technology-based solutions. And technology does play a key role. For example, the use of robust encryption technologies — such as public-private key approaches — is critical for protecting PHI.
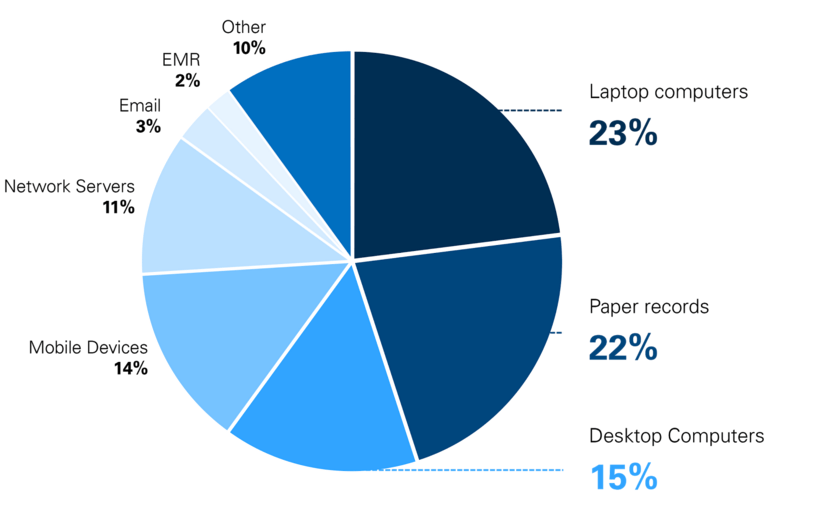
Figure 2. Sites of HIPAA Breaches
“Portable device theft” was the number one cause of major HIPAA violations in 2014, accounting for half of all the violations. As the professional use of personal mobile devices and “BYOD” policies proliferate, it is important to remember to account for the security of these devices in your HIPAA compliance initiatives.
Source: HIPAAJournal.com
But organizations also need to focus on issues from a people and a process perspective, since a large portion of security lapses are due to people-related vulnerabilities. Managing the risks associated with people requires particular focus on permissions — addressing the “who”, “when”, and “where” questions related to PHI access — as well as ongoing training and education to minimize risky behaviors.
From a process perspective, the first step is to map PHI as it moves through your system — how it travels, where it is stored, and mostly importantly, how it is integrated with your overall business processes. By isolating PHI to critical use cases, your organization will reduce the scope and complexity of HIPAA compliance.
Next, compare your current data security and privacy procedures against requirements outlined in the HIPAA/HITECH Acts, including change control, data security and information lifecycle management, data center security, encryption and key management, governance and risk management, identity and access management, security incident management, and threat and vulnerability management. Armed with a general understanding of your position relative to the requirements, you can now create a plan of action for achieving compliance — either internally or externally.
