As digital transformation accelerates across healthcare, biometric security — the use of unique physical or behavioral traits, such as fingerprints, facial features or iris patterns, to verify identity — is emerging as a compelling alternative to traditional password‑based systems.
Healthcare professionals evaluating this shift must understand the current landscape of biometric adoption as well as the advantages, drawbacks and the careful steps required for a successful transition to
Read More
Healthcare Cybersecurity | Healthcare Data Security | Ransomware | Hospital Security Breaches
How to Run a High-Impact Healthcare Cybersecurity TTX
A well-orchestrated healthcare cybersecurity tabletop exercise (TTX) can greatly benefit any healthcare organization. Unfortunately, some TTXs are chaotic and unproductive. When 25 hospital leaders are tied up in a disorganized TTX for four hours, that’s 100 hours of lost productivity.
Here are some tips for how to conduct successful healthcare TTXs that can dramatically improve your preparedness for cyber crises:
Choose your invitations carefully – I’ve been in tabletop exercises that
Read More
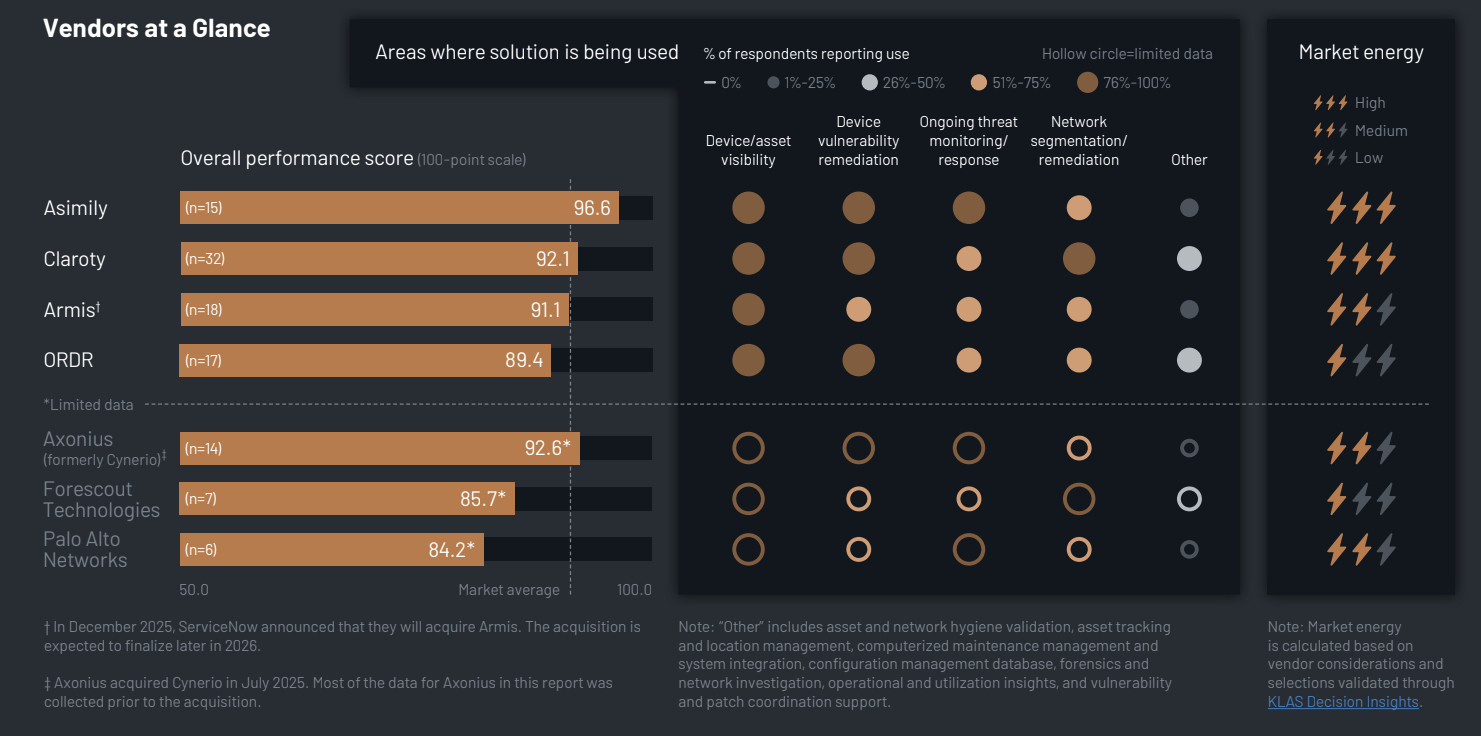
KLAS Healthcare IoT Security 2026: Top Vendors Rated for Risk Reduction and ROI
What You Should Know:
A new 2026 report from KLAS Research signals a major shift in the healthcare IoT security market: hospitals are no longer satisfied with just "seeing" their devices—they demand measurable risk reduction. The report names Asimily and Claroty as the market leaders with the highest energy, driven by their ability to deliver tangible outcomes like automated remediation and strong segmentation. Conversely, legacy players are facing scrutiny over complexity and training
Read More
How Legacy Active Directory Creates Ransomware Risks for Hospitals
In early 2024, the Ann & Robert H. Lurie Children’s Hospital of Chicago faced a catastrophic cyber incident. Between January 26 and 31, attackers infiltrated the network, forcing the shutdown of phones, email, and critical patient systems including the EHR and online portal. Nearly 800,000 individuals were later notified that their personal and medical data had been compromised. While the precise attack vector was not confirmed, the episode illustrates how outdated identity infrastructure,
Read More
Is Your Agency Next? Why Behavioral Health Leaders Can’t Ignore Cybersecurity
Many behavioral health agencies lack adequate controls to address and recover from a cybersecurity incident. What these agencies need are capabilities such as adequate backup and recovery, managed detection and response (MDR), security information and event management (SIEM), data loss prevention and other key security elements. Without these tools, agency leaders cannot identify a security incident and remedy or recover their IT environment.
In a 2024 report, the Ponemon Institute, an IT
Read More
Report: 52% of Healthcare Email Breaches Involve Microsoft 365 as “Silent Fallback” Exposes Patient Data
What You Should Know:
- A new report from Paubox reveals that email remains the number one source of HIPAA breaches, with 107 incidents reported in the first half of 2025 alone.
- The analysis identifies a critical flaw in popular platforms like Microsoft 365, which prioritize message delivery over security, often stripping encryption without alerting the sender. With the OCR proposing to upgrade encryption from an "addressable" to a "required" safeguard, healthcare organizations
Read More
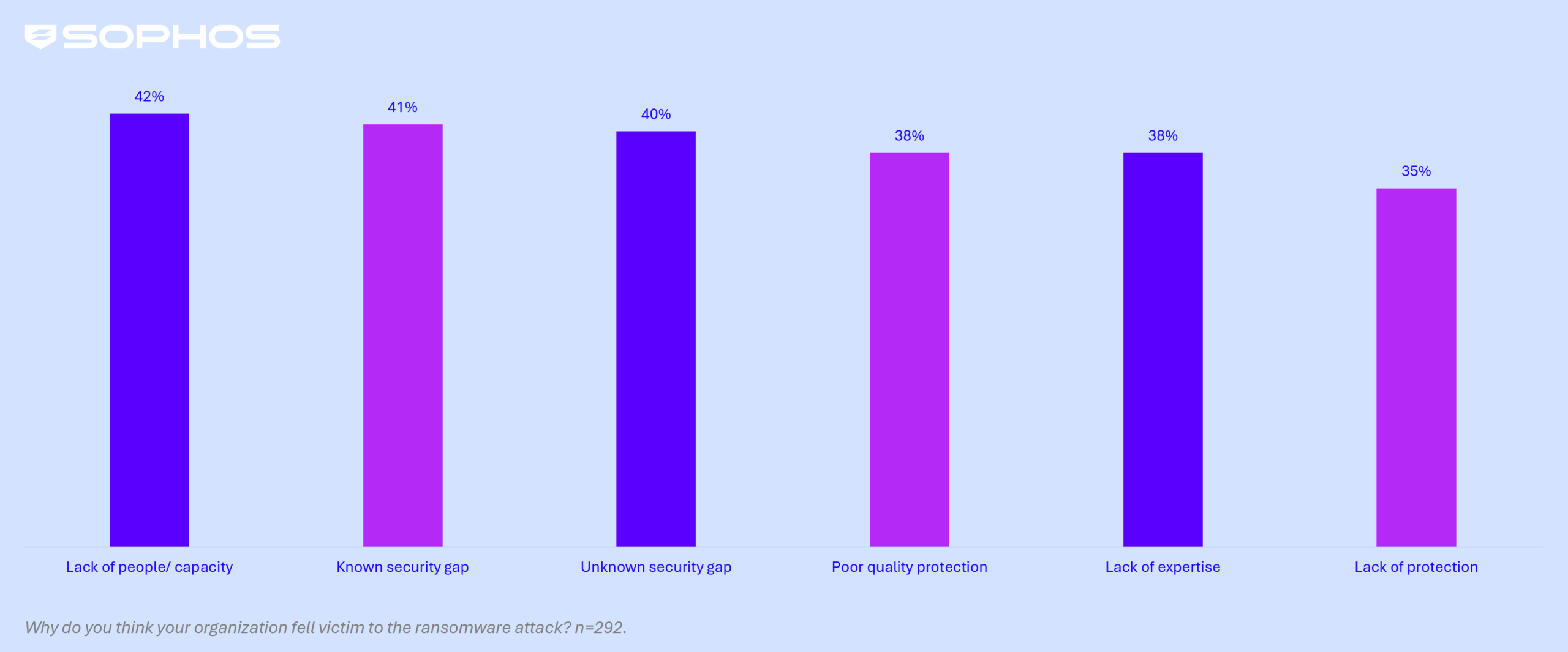
State of Ransomware in Healthcare 2025: Exploited Vulnerabilities Top Cause, Staff Capacity Biggest Weakness
What You Should Know:
- Sophos's State of Ransomware in Healthcare 2025 report reveals exploited vulnerabilities are now the leading technical cause of attacks (33%).
- The study highlights a sector becoming more resilient to encryption but facing soaring extortion-only attacks and high pressure on IT teams.
Root Causes Shift: Capacity Gaps and Exploited Vulnerabilities Lead
The latest Sophos study, based on the experiences of 292 healthcare providers, shows a significant
Read More
Cyber Resilience is Patient Safety: Why Healthcare Organizations Can’t Ignore Backup and Instant Recovery
Healthcare is under siege. Over the past five years, the sector has seen a 256% rise in cybersecurity breaches, as attackers grow more aggressive, more advanced and more relentless. Ransomware, phishing and supply chain attacks are evolving faster than most security teams can keep up with, and as a result, hospitals, clinics and care facilities are feeling the strain.
The reason? Healthcare is more connected than ever before. From bedside monitors and other internet of medical things (IoMT)
Read More
6 Strategies for Healthcare Executives to Elevate Cyber Resilience
What You Should Know:
- Healthcare organizations are facing an unprecedented cyber threat landscape, making the need to elevate cyber resilience to a strategic business priority more urgent than ever.
- According to the “US Healthcare Cyber Resilience Survey” released by Ernst & Young LLP (EY US) and KLAS Research, the risks posed by sophisticated cyber threats are directly compromising patient care, business operations, and financial stability.
Widespread Impact and
Read More
Thirdwayv and Medcrypt Partner to Standardize Cybersecurity for Connected Medical Devices
What You Should Know:
- At the Diabetes Technology Society Conference (DTM 2025), Thirdwayv Inc. and Medcrypt Inc. announced a strategic agreement to jointly advance cybersecurity and interoperability standards and solutions across the connected medical device ecosystem.
- The partnership seeks to address the increasing regulatory and operational demands for robust, life-cycle-spanning medical device security.
End-to-End Compliant Security Solution
The alliance brings together
Read More